How To Filter Out Sip Register In Wireshark
1. Decode TLS
First you need the private key used by you server.
Take the private key and save it on your PC. It should look like this:
-----BEGIN PRIVATE KEY-----
MIIEvwIBADANBgkqhkiG9w0BAQEFAASCBKkwggSlAgEAAoIBAQDXvcHGyQI7oUeQ
k1a38PMYoC9Eh+brPbOWtJh3UMkx/5jJ5AWyT4Isw2eOR94u2fsC0SZ3aqnPWQzO
...
JHAjJPm1zRGQFjGgVmDKPNrbQQQDf0ONDiOW7RcscYU4op8ou7U4o9q3Vxbscnru
BoiifdgCcKeYBnRIIFbxtLCR3Q==
-----END PRIVATE KEY-----
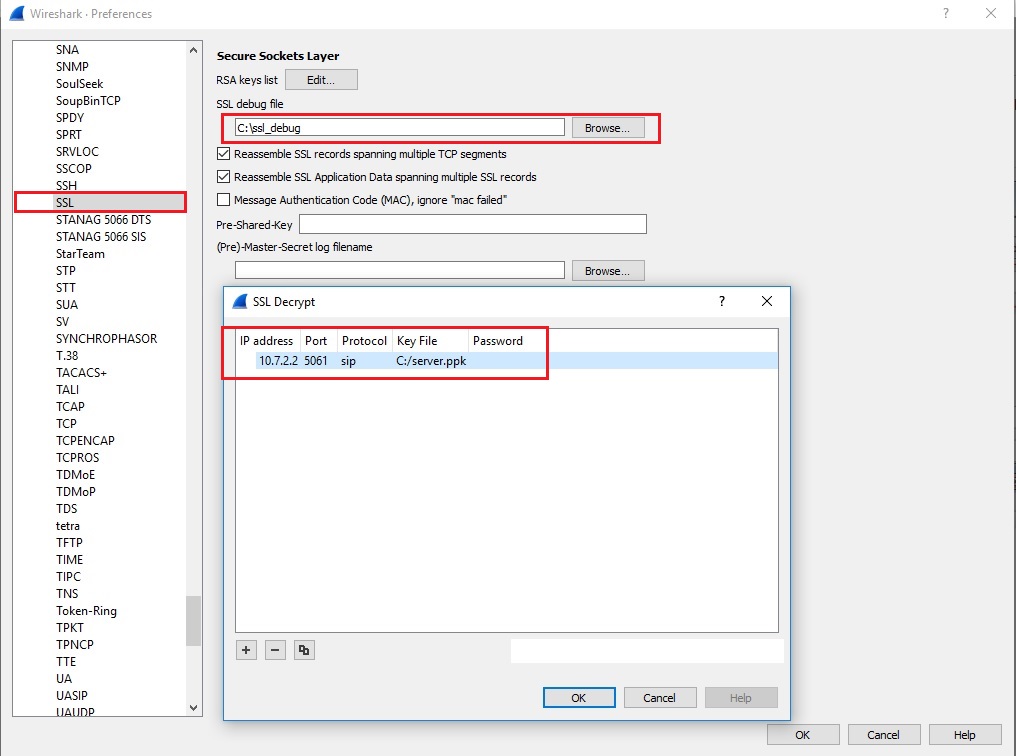
Open Wireshark and go to Edit >> Preferences >> Protocols >> SSL >>Edit and do the exact setup you can see below. Use the file created earlier with the private key.
Now, Wireshark cannot decode the capture without the SSL handshake between the phone and the server included in the capture. The handshake looks like this:

This SSL handshake occurs during each client Registration (phone reboot is required) and following each TCP handshake.
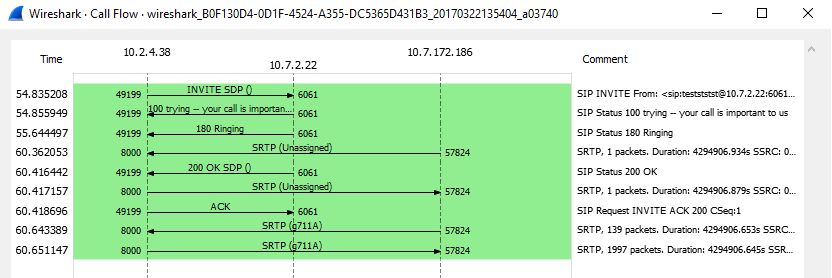
At this point, the entire call flow should be visible:
2. Obtain the keys and an RTP stream for decryption
The keys used for encrypting the RTP stream can be found in the SDP portion of a SIP packet. The keys for the calling party can be found in the SIP INVITE message, and the keys for the called party can be found in the SIP 200 OK message. It's helpful to first sort by SIP in Wireshark, as seen below:
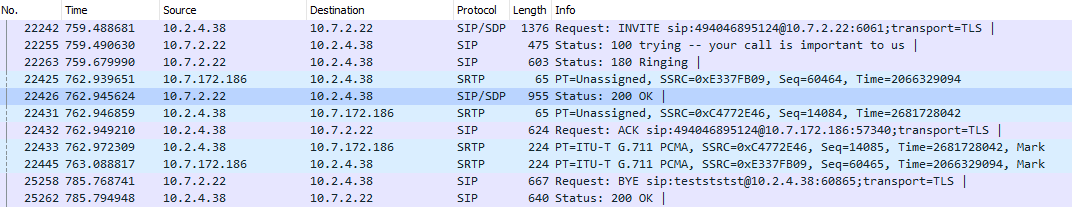
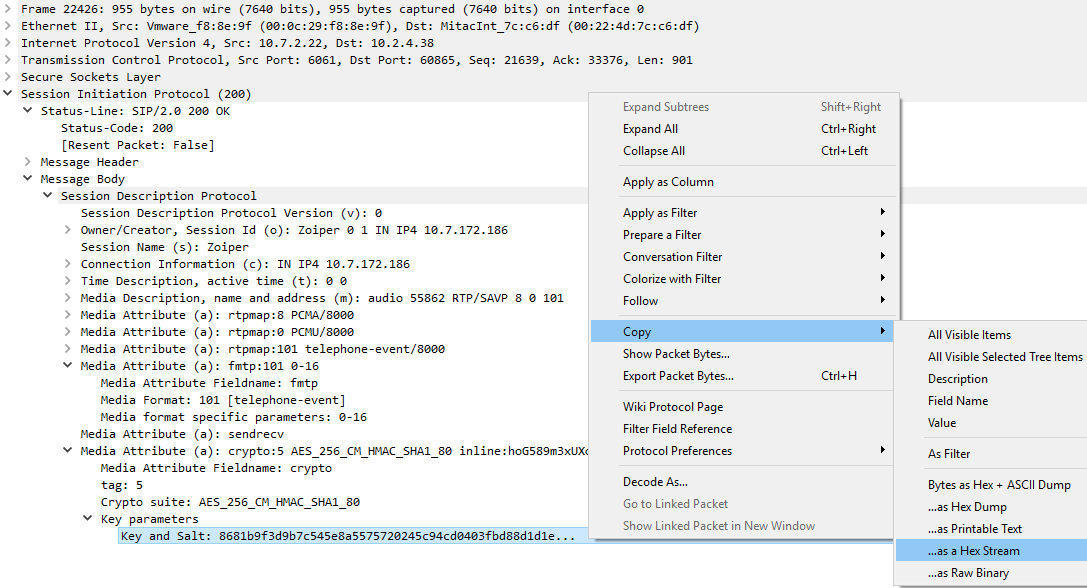
In this example, the calling party is 10.2.4.38, and the called party is 10.7.172.186. For this tutorial, we are only going to decrypt one side of the conversation, namely that of the called party (10.7.172.186). To obtain the key for the called party, we can simply expand the SDP portion of the 200 OK message, which is frame number 4. Below, we can see that the AES_CM_256_HMAC_SHA1_80 crypto suite is used and the "key and salt" is in plain view, with a value of "8681b9f3d9b7c545e8a5575720245c94cd0403fbd88d1d1e...."
.You can easily obtain the key and salt value in Wireshark by right-clicking on the field and selecting Copy > ..as a Hex Stream.
Now that we have the key and salt necessary for decryption, we need to isolate a single RTP stream. Since this is a simple example, with only one RTP stream being sent by each side (just one audio stream), we can do this with a simple Wireshark filter based on IP and protocol, as seen below:
The individual stream can be saved by navigating to File > Export Specified Packets. Ensure that only the Displayed packets are exported, and change the file type to ".pcap", instead of ".pcapng".
3. Decrypt the RTP stream with rtp_decoder (cisco libsrtp)
To perform decryption with the rtp_decoder test tool simply download or clone the cisco/libsrtp project from GitHub:
git clone https://github.com/cisco/libsrtp
cd libsrtp/
./configure
make
cd test/
./rtp_decoder -a -t 10 -e 256 -k 8681b9f3d9b7c545e8a5575720245c94cd0403fbd88d
1d1e562e856ca5b04b8c0f84ff838d97c40a867d6c9b663c * < ./srtp_single_stream.pcap | text2pcap -t "%M:%S." -u 10000,10000 - - > ./srtp_decrypted.pcap
./rtp_decoder --help Using libsrtp2 2.1.0-pre [0x2010000] usage: ./rtp_decoder [-d <debug>]* [[-k][-b] <key> [-a][-e]] or ./rtp_decoder -l where -a use message authentication -e <key size> use encryption (use 128 or 256 for key size) -g Use AES-GCM mode (must be used with -e) -t <tag size> Tag size to use (in GCM mode use 8 or 16) -k <key> sets the srtp master key given in hexadecimal -b <key> sets the srtp master key given in base64 -l list debug modules -f "<pcap filter>" to filter only the desired SRTP packets -d <debug> turn on debugging for module <debug> -s "<srtp-crypto-suite>" to set both key and tag size based on RFC4568-style crypto suite specification How To Filter Out Sip Register In Wireshark
Source: https://www.zoiper.com/en/support/home/article/162/How%20to%20decode%20SIP%20over%20TLS%20with%20Wireshark%20and%20Decrypting%20SDES%20Protected%20SRTP%20Stream
Posted by: dennishouncest.blogspot.com

0 Response to "How To Filter Out Sip Register In Wireshark"
Post a Comment